- Back to Home »
- Attacks , Ethical Hacking »
- Teardrop Attack : What Is It And How Does It Work?
Posted by : Sivapriya
Tuesday 28 June 2016
Teardrop attack is a type of Denial of Service (DoS) attack which
exploits the fragment offset field in the IP header to produce buggy fragments
which are then delivered to the target machine. Unable to rearrange the
fragments, the victim keeps on accumulating the fragments until it crashes.
As the
name suggests, the Teardrop Attack works gradually by sending the fragmented
packets to a target machine. It’s a type of a denial-of-service (DoS) attack which overwhelms the target machine with the
incomplete data so that the victim crashes down.
In Teardrop Attack, fragmented packets that
are sent in the to the target machine, are buggy in nature and the victim’s
machine is unable to reassemble those packets due to the bug in the TCP/IP
fragmentation.
In
this way, the packets keep on getting accumulated over the victim’s machine and
finally due to the buffer overflow, the target machine crashes down.
How Teardrop Attack works?
Here, I am taking a
reference from the Juniper’s technical publication to illustrate how does it
work —
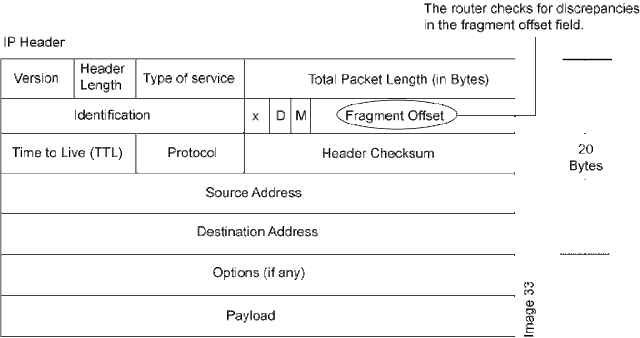
As
you can see in the above figure of IP header, which operates at the network layer, there is
a field called fragment offset field.
Teardrop Attack and Fragment Offset:
Understand it like this — When a large amount
of data is sent across the internet, the data is broken into the smaller
fragments. Each of these fragments is assigned a number. When they reach
the receiving end, these fragments are rearranged to reproduce the original
data or message.
To identify the sequencing of the fragments,
the fragment offset field holds the necessary information using which the
target machine rearranges the sequence.
However, in the Teardrop Attack, the fragment
offset field is made buggy by the hacker so the victim’s machine is unable to
find the relative fragments.
So, as the name suggests, the buggy packets
keep on accumulating at the victim’s side like teardrops and ultimately it
leads to the machine crash.
However,
modern networking devices can
detect this discrepancy in a fragmented packet. Once they detect the problem,
they simply drop the packet.
For More Details Contact :
Redback IT Academy
#AL 24 , TNHB Phase III,
Sathuvacheri
Vellore.
Contact : +91 8189985559