Archive for April 2018
Cyber Security - Meaning | Elements | Threats | Importance
INRODUCTION :
Cybersecurity is the body of technologies, processes and practices designed to protect networks, computers, programs and data from attack, damage or unauthorized access. In a computing context, security includes both cybersecurity and physical security.
Ensuring cybersecurity requires coordinated efforts throughout an information system.
Elements of cybersecurity include:
- Network security
- Application security
- Endpoint security
- Data security
- Identity management
- Database and infrastructure security
- Cloud security
- Mobile security
- Disaster recovery/business continuity planning
- End-user education
One of the most problematic elements of cybersecurity is the quickly and constantly evolving nature of security risks. The traditional approach has been to focus most resources on the most crucial system components and protect against the biggest known threats, which necessitated leaving some less important system components undefended and some less dangerous risks not protected against. Such an approach is insufficient in the current environment.
Some of the threats are outlined below in more detail.
Cyberterrorismis the disruptive use of information technology by terrorist groups to further their ideological or political agenda. This takes the form of attacks on networks, computer systems and telecommunication infrastructures.
Cyberwarfareinvolves nation-states using information technology to penetrate another nation’s networks to cause damage or disruption. In the U.S. and many other nations, cyberwarfare has been acknowledged as the fifth domain of warfare (following land, sea, air and space). Cyberwarfare attacks are primarily executed by hackers who are well-trained in exploiting the intricacies of computer networks, and operate under the auspices and support of nation-states. Rather than “shutting down” a target’s key networks, a cyberwarfare attack may intrude into networks to compromise valuable data, degrade communications, impair such infrastructural services as transportation and medical services, or interrupt commerce.
Cyberespionage is the practice of using information technology to obtain secret information without permission from its owners or holders. Cyberespionage is most often used to gain strategic, economic, political or military advantage, and is conducted using cracking techniques and malware.
More Common Threats are :
Ransomware
Ransomware is a type of malicious software. It is designed to extort money by blocking access to files or the computer system until the ransom is paid. Paying the ransom does not guarantee that the files will be recovered or the system restored.
Malware
Malware is a type of software designed to gain unauthorized access or to cause damage to a computer.
Social engineering
Social engineering is a tactic that adversaries use to trick you into revealing sensitive information. They can solicit a monetary payment or gain access to your confidential data. Social engineering can be combined with any of the threats listed above to make you more likely to click on links, download malware, or trust a malicious source.
Phishing
Phishing is the practice of sending fraudulent emails that resemble emails from reputable sources. The aim is to steal sensitive data like credit card numbers and login information. It’s the most common type of cyber attack. You can help protect yourself through education or a technology solution that filters malicious emails.
THE IMPORTANCE OF CYBER SECURITY
Cyber security is important because government, military, corporate, financial, and medical organizations collect, process, and store unprecedented amounts of data on computers and other devices.
A significant portion of that data can be sensitive information, whether that be intellectual property, financial data, personal information, or other types of data for which unauthorized access or exposure could have negative consequences.
Organizations transmit sensitive data across networks and to other devices in the course of doing businesses, and cyber security describes the discipline dedicated to protecting that information and the systems used to process or store it.
As the volume and sophistication of cyber attacks grow, companies and organizations, especially those that are tasked with safeguarding information relating to national security, health, or financial records, need to take steps to protect their sensitive business and personnel information.
As early as March 2013, the nation’s top intelligence officials cautioned that cyber attacks and digital spying are the top threat to national security, eclipsing even terrorism.
To more about Cyber Security Training and Information Security contact :
Redback IT Solutions Pvt Ltd.,
No: 5/X2 Hari Ohm , 2nd Street,
Phase III, Sathuvachari, Vellore.
Contact : +91 8189985551.
What Is ‘Trustjacking’? How This New iOS Vulnerability Allows Remote Hacking?
Do you plug in your iPhone into someone else’s laptop for a quick charge? If yes, you might be at the risk of ‘trustjacking’ where your device could be hacked remotely.
This new vulnerability called trustjacking exploits a convenient WiFi feature, which allows iOS device owners to manage their devices and access data, even when they are not in the same location anymore.
How does Trustjacking works?
When iPhone users plug into the USB port on someone else’s computer, iOS asks them whether the computer can be trusted or not. It also prompts that the computer will gain access to their data on granting permission.
Upon granting the permission, the user allows the computer to communicate with the iOS device through iTunes Wi-Fi Sync feature. While this feature is quite helpful but the researchers at Symantec say that it leaves your phone open to the trusted computer.
This computer can be used to access photos, messages, any sensitive data, add malicious apps or even perform administrative tasks without seeking any further authorization from the iPhone owner. Hence the name “trustjacking.”
It is notable that while the initial setup requires connecting a device physically through the USB cable, the phone can be accessed even after disconnecting it with no notifications to the iPhone owners.
So how to stop Trustjacking?
As there is no way of deauthorizing one laptop after giving access, you will have to revoke access to all the authorized laptops. Just go to Settings, tap on General and find Reset option. Select Reset Location & Privacy option and enter your passcode to deauthorize all devices at once.
How To Check If Your Facebook Data Was Leaked To Cambridge Analytica?
Facebook has taken upon itself to notify all the 87 million victims of Cambridge Analytica Scandal, whose data may have been leaked by creating a link at the top of their News Feed.
Update: In case you haven’t been able to spot the link at the top of your News Feed, you can visit this link and check if your data was passed on to Cambridge Analytica in one way or the other. Fortunately, I got this: “Based on our available records, neither you nor your friends logged into “This Is Your Digital Life.”
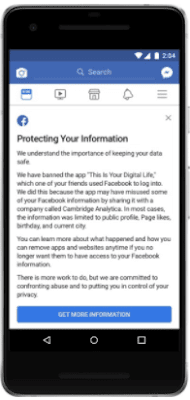
Starting from April 9, users will be able to a see a link titled “Protecting Your Information” on their News Feed. Here, you can find out which apps are connected to your Facebook feed and what kind of information you have shared with those apps.
In case you no longer use an app or wish to stop sharing data with them, Facebook will provide you the option to disable those apps and completely remove third-party access.
Moreover, users whose data was leaked to Cambridge Analytica will receive an additional notice from the company. There are three versions of the messages that are being sent to Facebook users based on whether their data was usurped by the app “This Is Your Digital Life.”
In case of data leak caused by direct logging into This Is Your Digital Life app by a user, the following message would be displayed on the screen.
If a user’s data was leaked due to a friend who logged into the app, this message given below would be displayed. It says that your basic information such as public profile, page likes, birthday, etc., have been shared.
For users whose data remain unharmed, Facebook will send the following message along with the new privacy control settings.
Although Facebook is taking corrective measures, yet scores of people feel unsafe on the platform and are shutting down their accounts as details of the data leak emerged. If you feel the same,delete your account permanently.
Artificial Intelligence And It’s Role In Mobile App Development
Since mobile app development is transforming our lives by turning unfeasible things into reality, Artificial Intelligence is not only a hot topic in the field of science but also a topic of exploration and development in the business industry, purposely in the industry of mobile app development.
These days, AI is not limited to Apple’s Siri anymore, but it is growing much more than our imaginations and the time is here to see mobile app developers putting more of artificial intelligence together in their endeavors.
Introduction to Artificial Intelligence :
Well, AI or artificial intelligence is the branch of science that usually design and develop intelligent machines that totally work and react like humans. It is a brilliant way of impacting aptitude to advanced machines so they can troubleshoot problems themselves even more accurately, efficiently and rapidly than before.
A big number of well know companies and organizations are successfully using artificial intelligence in their business operations not only to accomplish their business process efficiently but to boost the productivity as well.
As mobile app development companies are using AI in business app development projects, it can boost competency of a company or business as it provides more personalized, relevant and flawless customer services at the end. Companies can easily understand customer behavior just by using the data collected by artificial intelligence in mobile apps.
Role of AI in Mobile App Development :
Affirmative business growth and user engagement are the core factors that are proving the significance of the use of artificial intelligence in mobile app development services.
There are a lot of things that make huge difference between mobile apps developed with and without artificial intelligence such as
- Collection of users’ data by analyzing the behavior and usage pattern of the app.
- Use of the location, contacts and daily behavior to allow the app to serve users better than before.
- Generating the maximum revenues with satisfactory and user-friendly user interfaces.
There is nothing wrong to say that it is the time to experience big change in performances and process as we are now getting more AI and machine learning-driven apps from mobile app development companies. We have a lot of live examples of trending mobile app technologies in our mobile phones that are using artificial intelligence such as Google assistant, Siri and Contra etc.
Now in this digital age we can feel free to say that increasing growth of artificial intelligence is empowering new opportunities and possibilities in mobile app development services. A mobile application developed with artificial intelligence is designed in a way that it can make right decisions itself, resource your finances and most importantly consider advantages or disadvantages for you. Similarly, devices and machines created with artificial intelligence technology have beaten the humans in almost all walks of life.
In the same way, increased use of AI in the mobile app development services has enabled the mobile users to entirely refill the existing user-experience with an amazing one. Due to the availability of artificial intelligence in mobile application development, gigantic amount of data is available to the businesses or organizations in terms of customer spending hours, purchasing behavior, user interest and so on that can be used for productive business decision making process.
Thorough this way, mobile app technology can understand the customer behavior quickly and provide thorough insights of the customer preferences to the concerned entities for making the business process more efficient accordingly.
Predictive reply is one of the plus points for mobile app developers that they can use to make their apps better than ever as it is the communication between user and the device where artificial technology used in the app understands the conversation and responds it accurately without mixing things together. For example, Gmail app (powered by Google) has been designed with a latest feature of Smart Reply that uses artificial neural networks to arrange and send suitable responses to the emails received.
Artificial intelligence and its role in mobile app development is just undeniable as it enables a business or brand to provide personalized user experience to make things easier and efficient. For instance, My Starbucks Barista is a mobile application and the user just have to tell the app what they want and the app would automatically place the order for its user based on the given partialities by its own.
Thursday 19 April 2018
Posted by Sivapriya
Facebook Admits: It Scans All Messages And Photos You Send On Messenger
Earlier this week, in an interview with Vox, Mark Zuckerberg tried to answer some hard questions put in front of him. In the same process, he ended telling about the ethnic cleansing issue in Myanmar and how Facebook detected people’s sensational messages sent via Messenger.
This sparked some obvious questions regarding Facebook’s Messenger-related data policies. Now we have answers as a result of Facebook’s statements given to Bloomberg.
The company told that it scans the Messenger conversations of all users to curb abuse on the social network. However, the company doesn’t use this private data for advertising purposes.
As per the content policies of the company, all content must be treated with same guidelines. So, all messages need to be scanned and automated tools are employed to flag a message or picture for review.
Explaining further, the company told that it needs to scan links as well to eradicate the threat of malware. Similarly, by scanning pictures, it aims to detect and flag child pornography.
In the wake of recent revelations, Facebook has also come up with its updated privacy policy. The new policy tries to explain the data usage in a more transparent manner.
“We explain the services we offer in a language that’s easier to read,” an official blog post reads. It also talks about a feedback collection process that’ll let you share what you think about the new changes.
Moreover, it has also been made clear that Instagram and Messenger apps follow the same data policy and content review rules.
Thursday 5 April 2018
Posted by Sivapriya